It’s recently come to my attention that many new users to Linux are unaware there are automatic updates available for their distribution. This has started to make it’s way into the UI but in many cases this isn’t yet possible which is unfortunate.
Updates are more important than ever to deliver security patches and keep system safe. So lets check the options.
KDE
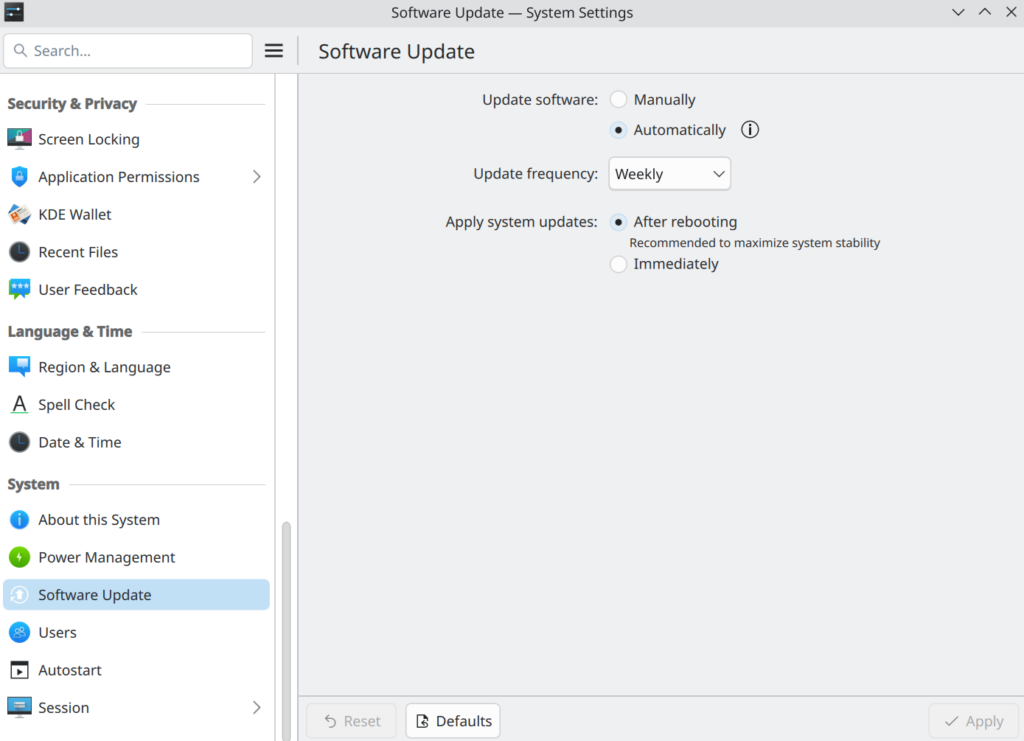
In KDE, provided your distribution has implemented it, as of KDE 6.3.4, you can go to Settings > Software Update and select your preferred auto-update options.
Gnome
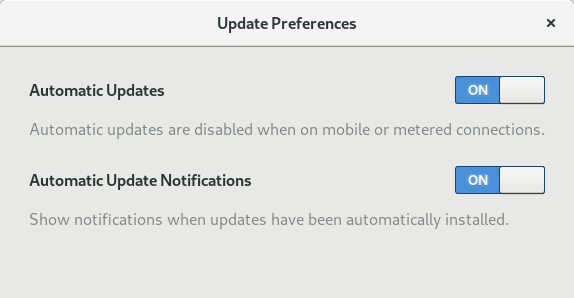
Gnome may be more hit or miss but as of Gnome 3.30 you can enable automatic updates. For now it appears this is limited to Flatpaks. https://blogs.gnome.org/hughsie/2018/08/08/gnome-software-and-automatic-updates/
DNF based distributions
As is the case with most things Linux this will require getting down and dirty with the command line. Trust me it’s not as daunting as it appears.
Information from https://docs.fedoraproject.org/en-US/quick-docs/autoupdates/
Install and settings of dnf-automatic
On a fresh install of Fedora with default options, the dnf-automatic RPM is not installed. The first command below installs this RPM:
sudo dnf install dnf-automaticBy default, dnf-automatic runs from the configurations in the /etc/dnf/automatic.conf file. These configurations only download, but do not apply any of the packages. In order to change or add any configurations, open the .conf file as the root user (or using sudo) from a terminal window.
sudo nano /etc/dnf/automatic.confA modification to automatic.conf to download all updates, apply them, and reboot could be:
[commands]
apply_updates=True
reboot=when-neededOmit reboot=when-needed to manually reboot. A full and detailed description of dnf-automatic settings is provided on the dnf-automatic page.
Run dnf-automatic
Once you are finished with the configuration, execute:
systemctl enable --now dnf-automatic.timerto enable and start the systemd timer.
Check status of dnf-automatic:
systemctl status dnf-automatic.timerPreconfigured Timers
Some special timer units are provided which override parts of the configuration file with some standard behaviors:
dnf-automatic-download.timer– Download, but not install updatesdnf-automatic-install.timer– Download and install updatesdnf-automatic-notifyonly.timer– Only notify of available updates via configured emitters in/etc/dnf/automatic.conf
A full and detailed description of dnf-automatic settings is provided on the dnf-automatic page.
APT Based Distributions
Information from https://wiki.debian.org/UnattendedUpgrades
sudo apt update
sudo apt install unattended-upgradesAfter installation, you can check to ensure that the unattended-upgrades service is running using systemctl:
sudo systemctl status unattended-upgrades.serviceOutput● unattended-upgrades.service - Unattended Upgrades Shutdown
Loaded: loaded (/lib/systemd/system/unattended-upgrades.service; enabled; vendor preset: enabled)
Active: active (running) since Mon 2022-02-14 17:51:49 UTC; 3h 4min ago
Docs: man:unattended-upgrade(8)
Main PID: 829 (unattended-upgr)
Tasks: 2 (limit: 1137)
Memory: 10.6M
CGroup: /system.slice/unattended-upgrades.serviceThe default configuration of unattended-upgrades will automatically retrieve bug fix and security updates for most of the packages included in the Ubuntu repositories. However, if you are using older versions of some packages in order to avoid upstream changes, or if your server uses third party package repositories in addition to Ubuntu’s, you can further configure the unattended-upgrades service.
Its configuration is stored in /etc/apt/apt.conf.d/50unattended-upgrades. Open this file using nano or your favorite text editor:
sudo nano /etc/apt/apt.conf.d/50unattended-upgradesThe file is well-annotated, and you can see many lines of code comments (beginning with //) explaining its functionality. The first configuration block handles which packages will be automatically updated, matching a template for Ubuntu package repository names. Files in the core repository and in the -security repository will be updated by default, but the lines containing the -updates, -proposed, and -backports repositories are commented out by default.
These repositories are disabled by default because they are more likely to contain breaking changes to your installed packages. In order to enable them for unattended upgrades manually, you can delete the // comment symbols from these lines.
/etc/apt/apt.conf.d/50unattended-upgrades
// Automatically upgrade packages from these (origin:archive) pairs
//
// Note that in Ubuntu security updates may pull in new dependencies
// from non-security sources (e.g. chromium). By allowing the release
// pocket these get automatically pulled in.
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}";
"${distro_id}:${distro_codename}-security";
// Extended Security Maintenance; doesn't necessarily exist for
// every release and this system may not have it installed, but if
// available, the policy for updates is such that unattended-upgrades
// should also install from here by default.
"${distro_id}ESMApps:${distro_codename}-apps-security";
"${distro_id}ESM:${distro_codename}-infra-security";
// "${distro_id}:${distro_codename}-updates";
// "${distro_id}:${distro_codename}-proposed";
// "${distro_id}:${distro_codename}-backports";
};
…Further down the file, there are a number of options with true / false configuration toggles. For example, there is a toggle to automatically reboot following the installation of packages that need a reboot in order to take effect. You could enable this option by removing the // comment symbol and changing false to true. However, doing so will cause your server to become unavailable at unpredictable intervals. If you enable this option be sure your applications or users can tolerate downtime.
/etc/apt/apt.conf.d/50unattended-upgrades
// Automatically reboot *WITHOUT CONFIRMATION* if
// the file /var/run/reboot-required is found after the upgrade
//Unattended-Upgrade::Automatic-Reboot "false";Save and close the file when you are done editing it. If you are using nano, press Ctrl+X, then when prompted, Y and then Enter.
If you made changes to the configuration, restart the unattended-upgrades service in order for it to take effect:
sudo systemctl restart unattended-upgrades.serviceYou should now have solutions in place to ensure all of the packages on your server receive essential security updates without any additional intervention. In the last step, you’ll learn how to keep your kernel updated, and how best to handle server reboots when they are necessary.
